IMS鉴权主要有:
- SIP Digest(SIP摘要):针对无ISIM卡的终端
- HTTP Digest(HTTP摘要):SIP协议的基本认证方式,用于UAS/SIP Proxy Server对UAC的单向认证
- IMS AKA(AKAv1_MD5、AKAv2_MD5(:对HTTP摘要认证的扩展,用于UE和IM CN网络之间的双向认证,同时协商得到UE和IM CN共享的完整性密钥IK(Integrity Key)和加密密钥CK(Ciphering Key),在UE和IM CN协商建立的IPSec SAs连接上提供完整性保护(Integrity Protection)和机密性保护(Confidentiality Protection)
IMS注册流程
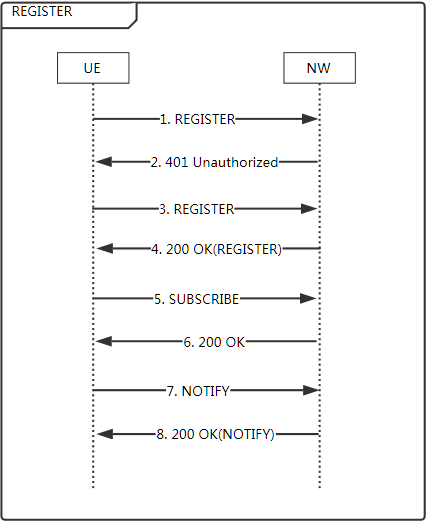
终端鉴权算法
目前终端都是使用的AKAv1_MD5算法,可以从UE的注册日志中确认。
2017 Jul 12 08:56:24.546 [B0] 0x156E IMS SIP Message -- IMS_SIP_REGISTER/UNAUTHORIZED ... WWW-Authenticate: Digest realm="ims.mnc000.mcc460.3gppnetwork.org",nonce="lAusUHute2JpIL+4+eBGVXfrphO9IQABazyikcth0XQ=",algorithm=AKAv1-MD5
AKA
AKA:Authentication and Key Agreement(身份验证和密钥协议),该机制是由IETF制定,并且被3GPP广泛采用于GSM/UMTS/LTE/IMS等技术中。详细可以参考 RFC 3310。
USIM参数和应用
| 参数 | 长度 | 备注 |
|---|---|---|
| K | 128bit | 密钥 |
| RAND | 128bit | 随机值 |
| SQN | 48bit | 序列号 |
| AMF | 16bit | 鉴权管理域 |
| MAC | 64bit | 消息鉴权码:f1k(SQN||RAND||AMF) |
| MAC-A | 64bit | 网络鉴权码,一般鉴权时为MAC |
| MAC-S | 64bit | 重同步鉴权码,=MAC |
| (X)RES | 64bit | 鉴权响应:f2k(RAND) |
| CK | 128bit | 加密密钥:f3k(RAND) |
| IK | 128bit | 完整性密钥:f4k(RAND) |
| AK | 48bit | 匿名钥匙:f5k(RAND) |
| AUTN | 128bit | SQN ⊕ AK || AMF || MAC |
| XDOUT | 128bit | K ⊕ RAND |
| CDOUT | 128bit | SQN || AMF |
符号含义
| 符号 | 备注 |
|---|---|
| = | 等于 |
| || | 连接运算,如0000 || 0001 = 00000001 |
| ⊕ | 异或运算,如0000 ⊕ 0011 = 0011 |
举例
| 参数 | 值 |
|---|---|
| K | 000102030405060708090a0b0c0d0e0f 00000000 00000001 00000010 00000011 00000100 00000101 00000110 00000111 00001000 00001001 00001010 00001011 00001100 00001101 00001110 00001111 |
| RAND | 6d06a714fe2def464562a53db0db7d50 01101101 00000110 10100111 00010100 11111110 00101101 11101111 01000110 01000101 01100010 10100101 00111101 10110000 11011011 01111101 01010000 |
| AMF | 8000 10000000 00000000 |
| SQN | 000000000001 00000000 00000000 00000000 00000000 00000000 00000001 |
XDOUT = K ⊕ RAND = 01101101000001111010010100010111111110100010100011101001010000010100110101101011101011110011011010111100110101100111001101011111 = 6D07A517FA28E9414D6BAF36BCD6735F XRES = f2(XDOUT,n) = 6D07A517FA28E9414D6BAF36BCD6735F CK = f3(XDOUT) = XDOUT循环左移8bits = 07a517fa28e9414d6baf36bcd6735f6d IK = f4(XDOUT) = XDOUT循环左移15bits = a517fa28e9414d6baf36bcd6735f6d07 AK = XDUT[b24,25,...70,71] = 17fa28e9414d CDOUT = SQN || AMF = 00000000 00000000 00000000 00000000 00000000 00000001 10000000 00000000 = 0000000000018000 XMAC = XDOUT[b0,1,...62,63] ⊕ CDOUT[b0,1,...62,63] = 6d07a517fa296941 AUTN = SQN ⊕ AK || AMF || MAC = 17fa28e9414c80006d07a517fa296941
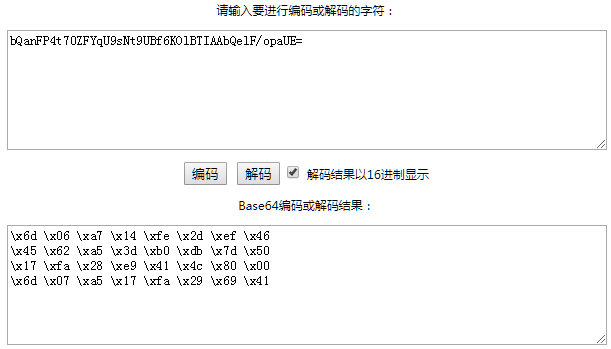
从SIP消息中我们读取下面的信息,分别为UAS发送给UAC的,和UAC回复UAS的响应。nonce = (RAND + AUTN + [服务器制定的信息] ) + BASE64编码。
WWW-Authenticate: Digest realm="ims.mnc000.mcc460.3gppnetwork.org", nonce="bQanFP4t70ZFYqU9sNt9UBf6KOlBTIAAbQelF/opaUE=", opaque="1f7e898d3940e21e23d82ffa7bfe9141", algorithm=AKAv1-MD5, qop="auth" Authorization: Digest username="460001234567890@ims.mnc000.mcc460.3gppnetwork.org", realm="ims.mnc000.mcc460.3gppnetwork.org", uri="sip:ims.mnc000.mcc460.3gppnetwork.org", qop=auth, nonce="bQanFP4t70ZFYqU9sNt9UBf6KOlBTIAAbQelF/opaUE=", nc=00000001, cnonce="1374676361", algorithm=AKAv1-MD5, response="8b8cad6c93b68b879594f8b731e3fcf4", opaque="1f7e898d3940e21e23d82ffa7bfe9141"
可以看到SIP消息中的nonce的值就是RAND + AUTN。
参考
3GPP TS 35.206